heartbleed 2014-04-09
In light of the recent heartbleed bug, I have taken an opportunity to review my server configuration and ensure that everything is up to snuff. To facilitate this, I used the wonderful Qualys SSL Labs tool. Their best practices seemed extremely reasonable to me so I set out to ensure I was following all of them
First of all, I had to make new server keys and certs because of the potential that they were compromised. Personally, I can never remember how to work the openssl command line tool so I have set up a makefile to do all that nonsense for me:
BITSIZE=4096
FILE=eatabrick.org
all: $(FILE).pem $(FILE).key dhparam.pem
chown http:http $(FILE).*
chmod 600 $(FILE).key
$(FILE).pem: $(FILE).csr intermediate.pem
@echo "Copy and paste the following into your CA:"
@cat $(FILE).csr
@echo "Paste the certificate from your CA here (^D to finish):"
@cat >$(FILE).pem
@cat intermediate.pm >>$(FILE).pem
$(FILE).csr: $(FILE).key
openssl req -new -key $(FILE).key -out $(FILE).csr
$(FILE).key:
openssl genrsa -des3 -passout pass:x -out $(FILE).pass.key $(BITSIZE)
openssl rsa -passin pass:x -in $(FILE).pass.key -out $(FILE).key
rm $(FILE).pass.key
intermediate.pem:
@echo "Paste any intermediate certs here (^D to finish):"
@cat >intermediate.pem
dhparam.pem:
openssl dhparam -out dhparam.pem $(BITSIZE)
clean:
rm $(FILE).* intermediate.pem dhparam.pem
This makes my life much easier since I can just make clean all when it's time
for new certs. The dhparam.pem rule is because nginx by default uses
openssl's default DH parameters which are only 1024 bit and that will weaken the
security of clients using ephemeral keys which kind of defeats the purpose.
With the certs in place, I have the following nginx configuration:
server {
listen 80 default;
listen [::]:80 default;
server_name eatabrick.org www.eatabrick.org;
rewrite ^/(.*) https://eatabrick.org/$1 permanent;
}
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name www.eatabrick.org;
ssl_certificate /etc/nginx/ssl/eatabrick.org.pem;
ssl_certificate_key /etc/nginx/ssl/eatabrick.org.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4:!3DES';
ssl_session_cache shared:SSL:10m;
ssl_dhparam /etc/nginx/ssl/dhparam.pem;
ssl_stapling on;
add_header Strict-Transport-Security max-age=31536000;
add_header X-Frame-Options DENY;
rewrite ^/(.*) https://eatabrick.org/$1 permanent;
}
server {
listen 443 ssl default;
listen [::]:443 ssl default;
server_name eatabrick.org;
ssl_certificate /etc/nginx/ssl/eatabrick.org.pem;
ssl_certificate_key /etc/nginx/ssl/eatabrick.org.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4:!3DES';
ssl_session_cache shared:SSL:10m;
ssl_dhparam /etc/nginx/ssl/dhparam.pem;
ssl_stapling on;
add_header Strict-Transport-Security max-age=31536000;
add_header X-Frame-Options DENY;
access_log /var/log/nginx/eatabrick.org.access.log;
error_log /var/log/nginx/eatabrick.org.error.log;
root /srv/http/eatabrick.org/htdocs/;
index index.html;
error_page 404 /404.html;
}
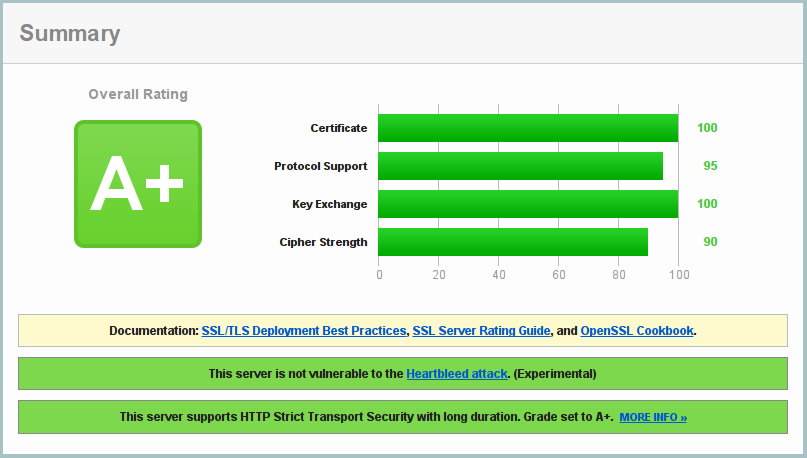
This configuration has netted me a coveted A+ from Qualys:
However, I did have to make some compromises to do this.
First, I have disabled use of SSLv3 (because it is broken). This precludes IE6 from accessing eatabrick.org. I cannot think of anything less controversial than this. If for some reason you need to support people using IE6 you should review your life choices. According to Qualys, this also precludes YandexBot 3.0, which is apparently a bot from a Russian search engine. This is more unfortunate than not supporting IE6 but not so much that I am going to use a broken protocol.
Second, as mentioned earlier, I am using 4096 bit DH parameters to match my 4096 bit key. This apparently precludes Java 6u45 from connecting. As far as I am aware Java 6 is no longer supported so it's probably time for any clients using this to upgrade to something less broken.
Lastly, I have excluded 3DES from the list of ciphers my server is willing to use. This was probably not entirely necessary since 3DES is not really broken but it does use 112 (or 108) bit keys which are a tad too small for my taste so it got the axe. This precludes IE8 on Windows XP from connecting. As with the other sacrifices, this product is no longer supported by its makers so I see no reason for it to be supported by me.